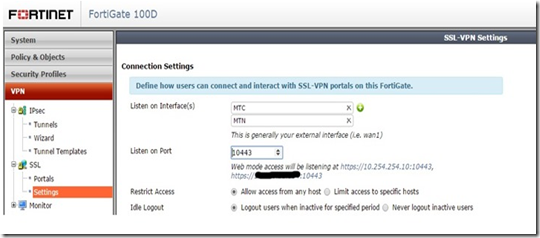
There is an potential issue when setting up SSL VPN to listen on multiple interfaces on FortiOS 5.2.2 (have not tested on earlier versions). When you create the first SSL VPN listener the Fortigate will automatically create a policy to allow SSL VPN traffic. Due to the way the information is presented one can be excused for thinking the unit will do it for additional listeners as well. The screenshot below shows how it looks when SSL VPN is enabled on multiple interfaces via the GUI:
These are the relevant bits taken from the configuration file:
config vpn ssl settings
set idle-timeout 900
set tunnel-ip-pools "SSLVPN_TUNNEL_ADDR1"
set tunnel-ipv6-pools "SSLVPN_TUNNEL_IPv6_ADDR1"
set source-interface "MTN" "MTC"
set source-address "all"
set source-address6 "all"
set default-portal "tunnel-access"
config authentication-rule
edit 1
set source-interface "MTN"
set source-address "all"
set groups "VPN"
set portal "full-access"
next
end
end
From the above it is clear that the listener has been added, but the authentication rule has not been updated. The fix is simple, just add an additional authentication rule via the CLI:
config vpn ssl settings
config authentication-rule
edit 2
set source-interface "MTC"
set source-address "all"
set groups "VPN"
set portal "full-access"
next
end
end
Your SSL VPN clients will now be able to connect on all interfaces specified in the GUI.
No comments:
Post a Comment