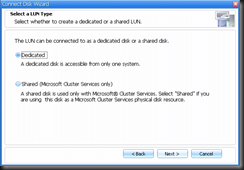
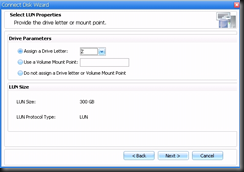
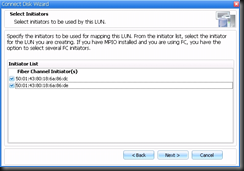
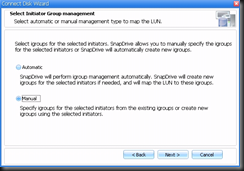
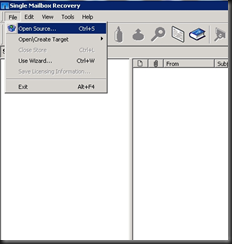
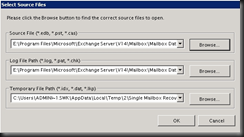
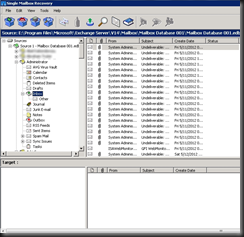
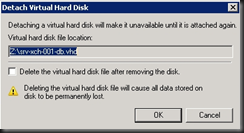
I've been working in IT for the best part of a decade, but only got into blogging and the whole social media thing in the last year or so. I really love doing what I do and sharing it with others, but in putting yourself out there you begin to realise how important ethics are. There is absolutely no difference between me and the next blogger, apart from the quality of the content one puts up and credibility.
Then something dawned on me, credibility is not just something that should shine through in what you put out there for the public to consume, it is even more important to apply those principles in your day to day dealings. It was about at that time when I realised that true credibility is something that is exceedingly rare in IT, in my experience.
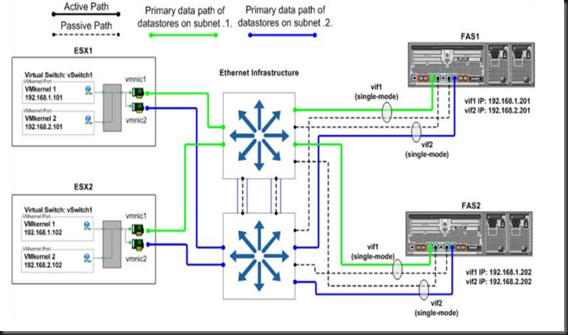
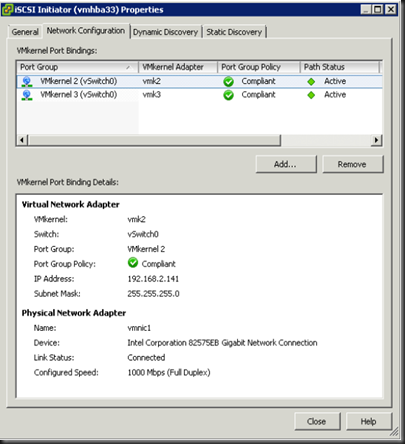
In my universe, a very quick way to loose credibility is to shoot down and bad mouth a product, vendor or technology you know nothing about. An example - I am in the somewhat unique situation where my job involves presales and architecting products from the two biggest storage vendors out there, namely EMC and NetApp. As if that's not enough, I also do the HP EVA portfolio. The storage field is hugely competitive, and this shows. I take my job seriously, so I make it my business to know the products I work with as well as possible.
For me it really is all about analysing the customers technical and business needs and consequently the application of the best technology for their given needs. And believe me, there is enough key differentiators between the various vendors, that when combined with the customers budgetary requirements that you will be able to determine a best-fit solution, and not this one-size-fits-all that most vendors fixate on. Unfortunately the amount of FUD and misinformation I've heard from people who really should know better is absolutely astounding. It gets to the point where the vendors are *actively* just advancing their own best interests with the client and their interests a distant second (or maybe I'm just naive, and that is how its supposed to work?).
As if that's not bad enough, I also do the entire lifecycle of both vSphere and Hyper-V, from pre-sales through to implementing and supporting. The amount of garbage I hear sprouted is enough to fill a landfill. Admittedly most of it comes from the vSphere-supporting side of the fence, but the Microsoft partners are quickly catching up. a Couple of examples I've heard is "Hyper-V does not do the equivalent of vMotion" or "the ESXi hypervisor is 50% faster then Hyper-V". Complete and utter bollocks in other words. As I said, the MS camp is quickly catching up and with the confidence and maturity that Hyper-V 3 will bring we'll see the MS guys giving as good as they get.
That being said, there will always be a bit of bias inherent in everyone. You will develop bias through your career, naturally leaning towards the solutions that you sell and implement. That is normal and there is nothing wrong with it. By all means do challenge the opposition's claims, ask them to backup their statements, ask for facts, see through the normal sales BS and question their value propositions.
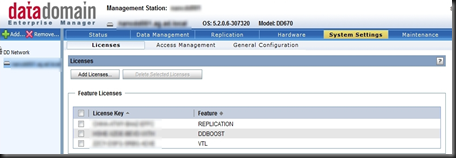
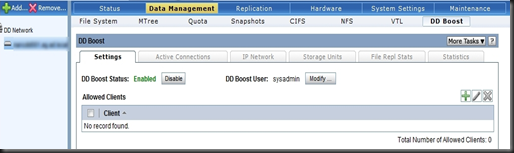
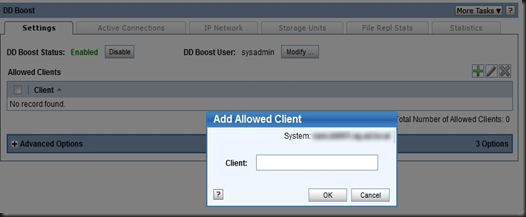
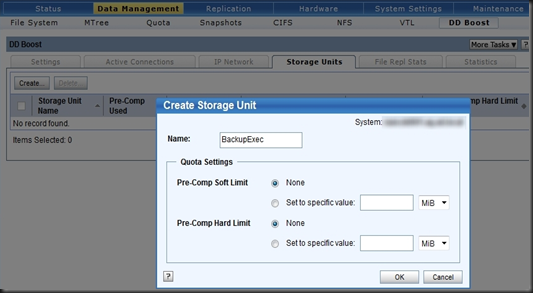
What is not right is the stuff I was talking about earlier. At the risk of repeating myself we should all try and avoid spreading FUD intentionally. Spreading it unintentionally is only slightly worse, because one should always verify claims before repeating it as gospel yourself. If NetApp, for example, tells me they scored eleventy billion marks on some benchmark whilst EMC flunked out I will investigate. EMC does knows a thing or two about storage - so there is bound to be a story behind the story. Conversely, if I hear a EMC partner starting with "No one can touch our Avamar / DataDomain dedupe / our ease of management / etc" my BS detector goes into overdrive.
The ultimate loser here is the customer who gets bombarded with noise and misinformation from all sides, whose job hinges on making the correct decision, who ultimately needs to put his trust in a vendor who is more interested in pushing a brand or technology which might or might not solve a problem and who needs to explain when a solution does not deliver.
We need to start putting the customer first in everything we do. In the short term it might not seem the easy / profitable thing to do, but in the long term you will be rewarded. Credibility is truly priceless, and once you give it up it is very, very difficult to regain.
Do The Right Thing.